Home >>Information Security Cyber Law Tutorial >Policies To Mitigate Cyber Risk
Policies To Mitigate Cyber Risk
Policies To Mitigate Cyber Risk
This chapter takes you through the various techniques put in place to minimize cyber risk. It is only with well-defined policies that it is possible to and the risks generated in cyberspace.
Promotion of R&D in Cybersecurity
The biggest problem we face today is the security of knowledge from miscreants due to the ever-increasing dependency on the Internet. It is therefore able to encourage cybersecurity research and development so that we can come up with robust solutions to mitigate cyber risks.
Cybersecurity Research
The area concerned with preparing solutions to deal with cybercriminals is cybersecurity research. In the future, with a growing number of internet attacks, advanced persistent threats, and phishing, a lot of research and technological advances are required.
Cybersecurity Research-Indian Perspective
India has seen enormous growth in cyber technology in recent years. This calls for an investment in cybersecurity research and development activities. With the advent of local cybersecurity companies, India has also seen many successful research findings that have been translated into firms.
Threat Intelligence
In India, research work to mitigate cyber-threats is already ongoing. To deal with cyber threats, there is a proactive response system in place. In order to fight threats in cyberspace, research and development activities are currently underway at various research organizations around the world.
Next Generation Firewall
Multi-identity-based expertise is also being worked on, such as the Next Generation Firewall, which provides companies with security information and helps them to apply the best-suited security controls at the edge of the network.
Secured Protocol and Algorithms
Protocol and algorithm research is a critical stage in centralizing cybersecurity at the technological level. It establishes the rules for sharing and processing information over cyberspace. In India, research at the protocol and algorithm level includes:—
- Protocols of Secure Routing
- Protocols for Efficient Authentication
- The Wireless Networks Improved Routing Protocol
- Protocol for Secure transmission power
- Algorithm for Attack Simulation, etc.
Authentication Techniques
The capability to encrypt and decrypt without a group security management system and file protection is provided by authentication techniques such as Key Management, Two Factor Authentication, and Automated Key Management. In order to enhance these authentication techniques, there is continuous research taking place.
BYOD, Cloud and Mobile Security
The study of security and privacy-related tasks on mobile devices has increased with the adoption of different types of mobile devices. Some of the areas where a lot of research is being done are mobile security testing, Cloud Security, and BYOD (Bring Your Own Device) risk mitigation.
Cyber Forensics
The use of analysis techniques to collect and recover data from a system or digital storage media is Cyber Forensics. Some of the unique areas in India where the research was conducted are:-
- Forensics on Disk
- Forensics for the Network
- Forensics of Mobile Devices
- Forensics for Memory
- Forensics in Multimedia
- Forensics of the Internet
Reducing Supply Chain Risks
It is formally necessary to describe supply chain risk as —
Any risk that an opponent can damage, write to it some malicious function, deconstruct a supply item or system's design, installation, procedure, or maintenance so that the whole function can be degraded.
Supply Chain Issues
The supply chain is a global problem and the interdependence between customers and suppliers needs to be established. It is important to know in today's scenario: What are the SCRM issues? And how to fix the issues?
A successful public-private relationship needs an efficient SCRM (Supply Chain Risk Management) approach. The government should have powerful authorities to deal with supply chain issues. In a number of areas, even the private sector can play a key role.
For the management of supply chain risks, we do not have a one-size-fits-all resolution. Costs for risk reduction can weigh differently depending on the product and the industry. To overcome risks associated with supply chain management, public-private partnerships should be encouraged.
Mitigate Risks through Human Resource Development
An organization's security policies can be effective, given all its employees understand their importance and show a strong commitment to their execution. Through applying the following few points, human resource directors will play a key role in keeping organisations safe in cyberspace.
Taking Ownership of the Security Risk Posed by Employees
As the risk factor is not taken seriously by most employees, hackers find it easy to target organizations. HR plays a key role in educating employees in this respect about the effect their attitudes and conduct have on the safety of the organization.
Ensuring that Security Measures are Practical and Ethical
A company's policies must be in sync with the way workers think and act. Saving passwords on systems, for instance, is a threat, but continuous monitoring will prevent it. The HR team is ideally qualified to advise if policies are likely to succeed and if they are suitable.
Identifying Employees who may Present a Particular Risk
It also happens that cybercriminals use the aid of a company's insiders to hack their network. It is therefore important to identify workers who could present a specific risk and have specific HR policies for them.
Creating Cybersecurity Awareness
Cybersecurity is also in its growth stage in India. This is the perfect time to develop an awareness of cybersecurity issues. From the grass-root level, it will be easy to build knowledge like schools where users can be made aware of how the Internet works and what its potential threats are.
Firewalls should protect all cyber cafés, home / personal computers, and office computers. Users should be advised not to invade illegal networks through their service providers or gateways. The risks should be boldly defined and the impacts should be highlighted.
Cybersecurity awareness subjects should be implemented to make it an ongoing method in schools and colleges.
By distributing the same through television/radio/internet advertisements, the government must formulate strong laws to implement cybersecurity and generate sufficient awareness.
Information Sharing
A law called the 2014 Cybersecurity Information Sharing Act (CISA) was proposed by the United States to strengthen cybersecurity in the country by improving the sharing of cybersecurity threat information. In every country, such laws are required to share threat data among people.
Cybersecurity Breaches Need a Mandatory Reporting Mechanism
An example of rising cyber-espionage and cyber-warfare is the recent malware called Uroburos / Snake. The latest trend is the stealing of classified information. It is unfortunate, however, that telecom companies/internet service providers ( ISPs) do not share information about cyberattacks against their networks. As a result, it is not possible to formulate a robust cybersecurity policy to counter cyberattacks.
This issue can be resolved by formulating a good cybersecurity law that can set up a regulatory system for notifications of compulsory cybersecurity violations by telecom companies / ISPs.
Infrastructures such as automated power grids, thermal plants, satellites, etc., are vulnerable to different types of cyber-attacks and will therefore alert the agencies to work on them with a breach notification program.
Implementing a Cybersecurity Framework
Given the fact that companies are investing in cybersecurity initiatives, there are still data breaches. In 2013, global cybersecurity investment by critical infrastructure industries was estimated to reach $46 billion, up 10 percent from a year earlier, according to Allied Business Intelligence Inc., according to the Wall Street Journal. "This calls for the cybersecurity framework to be implemented effectively."
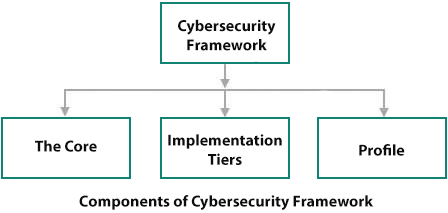
Components of Cybersecurity Framework
The Framework comprises of three main components :−
- The Core
- Implementation Tiers, and
- Framework Profiles
The Framework Core
The System Core is a collection of cybersecurity operations and applicable references that define, protect, detect, respond, and recover with five simultaneous and constant functions. To ensure the following, the system core has methods
- Develop and enforce procedures to secure the most important rights and assets of intellectual property.
- Have in place resources to identify any breach of cybersecurity.
- Recover, if and when one happens, from a breach.
The Implementation Tiers
The System Implementation Tiers describe the level of relevance and consistency used by an organization in the implementation of its security policies. The following four levels are in it.
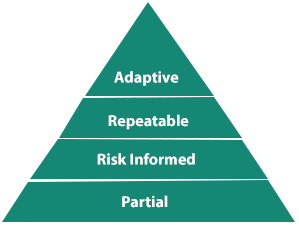
- Tier 1 (Partial) - The cyber-risk management profiles of the organisation are not specified at this level. At the level of the enterprise, there is a partial consciousness of the cybersecurity risk of the organization. The organization-wide approach to risk management has not been recognized.
- Tier 2 (Risk Informed) - Companies develop a cyber-risk management program at this level that is accepted directly by senior management. Senior management makes efforts to develop and execute cybersecurity-related risk management targets.
- Tier 3 (Repeatable) - The company conducts formal cybersecurity initiatives at this level, which are revised on a regular basis requirements. Its dependencies and associates are recognized by the organization. It also receives information from them, which helps to make decisions about risk-based management.
- Tier 4 (Adaptive) -The organisation adapts its "real-time" cybersecurity practices derived from previous and existing cybersecurity activities at this stage. The cybersecurity practices of the company will quickly respond to advanced threats through a process of incessant growth in the combination of advanced cybersecurity technologies, real-time collaboration with partners, and continuous monitoring of activities on their systems.
The Framework Profile
The Framework Profile is a tool that provides a platform for organizations to hold their cybersecurity program information. A profile enables organizations to express their cybersecurity program's objectives clearly.
Where do You Start with Implementing the Framework ?
The senior management, including the executives, should first get to know the system. After that, the directors should have a thorough discussion with the management about the Implementation Tiers of the organization.
Educating the framework's managers and workers would ensure that everybody knows its meaning. This is an essential step toward a vigorous security program being successfully implemented. Information on current System Implementations can help management with their own approaches.
